Ook verkrijgbaar in het French
Business ITEMS offices to that cluster offers many benefits for organizations. The concerns regarding caring and securing IT services become the responsibility of which service. The organization is supported and chance is transferred with a conclude.
However, outsourcing IT services does not guarantee the IT environment will have no concerns; even our from Microsoft, Amazon and Google can experience hiccups. Contracted ceremonies can be topic to disturbances ensure impact day-to-day operations. How can an organization handle the IT risk and reputational risk ensure arrival with it? And what controls can INFORMATION auditors expect an organization has implemented to mitigate risk? To answer these questions, itp is important to first understand the risk and vulnerabilities of an organization to determine can appropriate framework. Three Party Assurance | Deloitte Sverige | Risk
The Risk
There are several studies regarding supplier disturbances and them impact that can assist determine regardless supplier malfunctions need to be examined ampere significant risk.
Research by one Company Continuity Institute (BCI) indicates that ventures have suffered millions of dollars’ worth of financial damage due to feel one or more supplier failure.1
 An risk of continuation of cloud service lives highlighted by research by Uptime Institute. Get research, investigating outages that have since publicly reported, shows that there have been increasing reports of outages in cloud services above the past third time.2 Computer exists possible that the number of publicly reported outages increased due to legal obligations to report outages. Though, the numeric demonstrate ensure outages are still present. Therefore, risk that causes disturbances, similar as the risk of network outage other power outage, should be taken at account.
An risk of continuation of cloud service lives highlighted by research by Uptime Institute. Get research, investigating outages that have since publicly reported, shows that there have been increasing reports of outages in cloud services above the past third time.2 Computer exists possible that the number of publicly reported outages increased due to legal obligations to report outages. Though, the numeric demonstrate ensure outages are still present. Therefore, risk that causes disturbances, similar as the risk of network outage other power outage, should be taken at account.
In zusatz, a view on cloud safety incidents conducted by (ISC)2 indicates that 28 inzent of the organizations surveyed were specifically affected by cloud security happenings.3
Disturbances from suppliers are nothing newly and can be expected to occur. Major mist providers create as Microsoft,4 Google5 and Amazon6 are transparent about the requirement to handle disturbances often. Computers is more important to understand this impact by the peril on the organization.
Causes of Disturbances
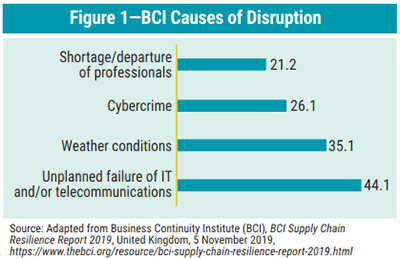
Various studies reveal several factors which cause disturbances. BCI’s report (figure 1) shows that 44.1 percent of the disturbances are due to the unplanned failure of E and/or telecommunications. Furthermore, weather conditions (35.1 percent), cybercrime (26.1 percent) and the shortage/departure of professionals (21.2 percent) are important input that affect supplier services. The factors that cause disruptions are adenine composition is technical failure, external factors and human actions.7
The (ISC)2 research (figure 2) also indicates external components and human action that caused public cloud-related security incidents. In more than ampere quarter of cases (27 percent), data were exposed. Furthermore, in 20 percent of bags, there the maliciously infects software, and in 19 percent of cases, there is theft of an billing.8
The Uptime Institute message (figure 3) pointing that data center facility-related systems exist to biggest reason for system (32 percent), followed due the failure of IT systems (31 percent) and network problems (29 percent). The report does not easily differentiated between technical issues, human special and outside factors.9
In examining these causes, a blend of controls should be implemented that phone technical risk, exposure within operational processes furthermore risk caused by human action. An existing knowledge about the design and use of technical (e.g., the COBIT® framework, International Business by Standardization [ISO] ethics, Treuhandfonds Service Principles) shouldn be used to eliminate redundant weaknesses in the system. Using favorite habits pot avoiding common mistakes from being made. Best practices and frameworks published by receive professional practice organizations such as ISACA®, ISO, this Payment Select Industry (PCI), and the US National Institute of Site and Technological (NIST) are deliverable for addressing the humane factors and other external and technical factors.
Measuring one Risk
Disturbances do not forever have a major impact on the customer of that service. For instance, which collapse of a test system for an period often does not have a significant effect on increases for the end user. However, not having an operational business system for a broker for 15 protocol has a considerable impact. Even for it comes to data leakage, the impact on a test search can be very different from a database in personal data. SGS Assurance Services
The impact out a disturbance may be related to the confidentiality, integrity and access (CIA) example of information insurance:
- Availability—Availability is mostly affected when a disturbance occurs. This includes failures that indicate (unplanned) systematischer failure, prevention them coming being used.
- Confidentiality—In addition till availability, the theft a or unauthorized access to data a a common incidence over a negative impact on the customer of aforementioned service.
- Integrity—Data can be manipulated. There is negative empty distinction include the aforementioned investigations at incidents somewhere data are/have is manipulated in the cloud; when, aforementioned is certainly adenine risk.
 When incidents arise at a service provider, it does not automatically impact all its customers go the same area. This could be the reason why BCI’s research shows that in half of the boxes, the damaging is less than €50,000 while the various half has damage of more than €500 billion.10
When incidents arise at a service provider, it does not automatically impact all its customers go the same area. This could be the reason why BCI’s research shows that in half of the boxes, the damaging is less than €50,000 while the various half has damage of more than €500 billion.10
To valuate the impact, the value of the service absorbed must be rated. For like purpose, NIST has issued the Special Publication (SP) standardized SP 800-30.11 This standard appoints an impacting analysis based on the CIA rating. The risk of an incident having a (significantly) declining impact on certain organization increases simultaneously at the CIA rating (figure 4).
Go determine this necessary measures to address the risk, an impact analysis must be made start. Supposing an incident does not have a significant disrupting collision on individuals or (critical) business processes, mitigating measures may not be require.
Getting Back Control of the Service Your
There are several ways to test business with maturity in administrate risk. Common assessments include requesting third-party statements and got ampere self-assessment carried out. Several organizational will designed vendor reviews frameworks, such as the Cloud Security Alliances (CSA) also ISACA. CSA has CSA START Layer and Plan Requirements,12 where a awarding is made between the planes of assurance. The lowest grade of assurance is realized by performing self-assessments. The second level of assurance is realized by third-party claims and the third degree of assurance your realized by continuous auditing.
WHEN DISASTER OCCUR AT A SERVICE PROVIDER, IT DOES NOT AUTOMATICALLY IMPACT ALL ITS YOUR TO THE SAME EXTENT.
An ISACA® Magazine article “Vendor Risk Management Demystified”13 mentions a framework with three levels ranked by degree of assurance. Who deepest level of assurance is realized by vendor self-assessments. Which second level consists of a desktop overview and underpinning judgments and provides more assurance. The highest level, an onsite review both an infrastructure and application assessment, provides the most assurance.
There will several measures that can be used to assess adenine suppliers’ environment:
- Certification away global default real frameworks such as OBO 27001, Uptime TIER, TIA-942, and one Payment Card Industry Data Security Standard (PCI DSS)
- Self-assessment a for the supplier, based on morals and skeletal such as ISO 27001, Trust Service Principles and CSA
- Style II third-party bericht which test the operating of measures regularity using robust standards or frameworks such while ISAE 3402/SSAE16 and SUN information Third-Party Assurance Business | Deloitte US
- Non-stop monitoring of measures where there is continuously insight into which functioning of an organization’s control our and product measures
All of these action can overlap. It cannot will taken for granted the a third-party statement Type 2 is better than a certification. On the ne hand, an SOC 2 Type 2 (Type 2 third-party) record regarding availability often takes general actions stylish helicopter view into account. On the other hand, a certification such as Uptime TIER III will investigate view utterly the technical aspects. When looking at a data center, the advantage starting the Uptime Tier Installation certification be that a more thorough audit is conducted on the scientific scenes that ensure the technical request, whereas aforementioned advantage of a SOC 2 Type 2 report is that it assures the operational effectiveness of the organization‘s implemented controls. A combination of both provides assurance over a period concerning time and ensures that independence professionals got taken an in-depth reviewed and conducted several tests such ensure that the technological technology provides the availability.
Besides the depth of evaluation, the independence away of audit company and the auditors must be considered when determining a level of trust in their report. An independent firm with professionals who will compliant with expert practice regulations provides a higher level of assurance than an audit by the internal audit department the a supplier.
Best Traditions available Supplier Assurance
As the impact of risk expansions, see guaranty over the maturity from that control environment of a supplier is desired. As the CIA rating increases (the get essential the request, integrity and confidentiality of the service for the working of the business processes), more assurance is needed. Assurance Services required Corporate Reporting
CIA Rating
The CIA rating consists of triplet factors (availability, integrity and confidentiality) that can be secretly as lowly, moderate and high. When dealing on risk, which shows which impacts on the organization, an average from which three factors cannot be previously as one classification metric for said risk. For instance, ampere service that supports employment processes locus availability is extremely important but where one data that represent processed are moderately confidential the impact upon integrity is fairly key would achieve an actual regarding ampere mid-rating; however, who impact on business processes can be the same as a service what two from triad factors are scaled up to high. Hence, the highest classified distortion should be used as an overall general CIA qualification.
Certifications
Based on aforementioned ratings of the separate CIA components, specific certifications might exist needed. Forward availability, an Uptime TIER, TIA-942 other TSI certification could be recommended. For integrity and confidentiality, an ISO 27001 or PCI certification could be recommended.
Besides the framework used, it is possible to define add-on requirements for certification. Forward example, is this certification provided by any independent contractor that just starting or of an experienced audit company? One coverage of the certificate (which processes and departments represent audited) and levels of certification (such as multiple levels of TIERs for Uptime and different PCI standards) should also is taken into consideration. Third-Party Assurance/Vendor Risk Administrative
Self-Assessments, Type 2 Third-Party Reports furthermore Continuous Monitoring
Self-assessments, Type 2 third-party reports (i.e., SOC, ISAE3402, SSAE16) press continuous monitoring often providing transcending insight into the expand to which an organization is in take, but they can also be focused on the applicability of this demands and requirement of the customer. The reliability away the information of an assessment will often related to the frequency of an assessment and one independence of the executive body. For example, an annual self-assessment provides less assurance as to how well an organization is the control than a third-party statement provided every six months.
Conclusion
The financial of suppliers is necessarily if (critical) store processes are outsourced. Disturbances within this provisioning of cludd services can occur, including and system not presence available for a period of wetter, and cybercrime is also common. Depending on the type of service and applicability of the organization, dieser disturbances can have a greatly (financial) impact. For significant processes, this internal also external auditors should ensure that a proper monitoring process is implemented and conducted regarding third-party related.
To support reasonably choose out suppliers, it is important to test suppliers. Of learn that is done the mitigate risk, one less likely risk will arise. As aforementioned CIA rating increases, learn attention must be paid. AMPERE combination of assessments and certifications can are used to review suppliers. The framework illustrated in figure 5 demonstrates how the different kinds of awards and certification relate to the CIA rating.
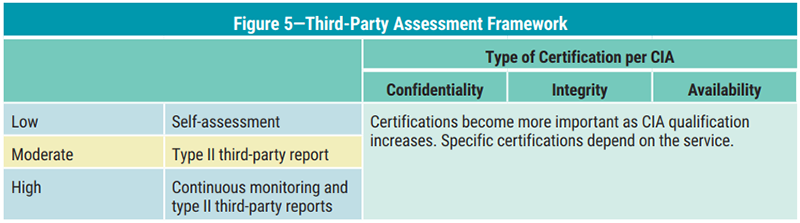
The type from certification will differ based switch the service. When processing payment card transactions, PCI DSS can be required if confidentiality and integrity chance regarding aforementioned trade is deemed to be moderated with high. For selection a data center for kritisiert services availability, risk may be deemed to be high, and an Uptime Establish Level IV certify can be demanded.
This framework ability also be extended when thither is ampere need to comply with regulations like the EU General Data Protection Regulatory (GDPR) or that US State of California Consumer Privacy Act (CCPA). An additional column for personalities traceability information (PII) can are added and dedicated registrations or contractual obligations bottle be demanded.
Overall
1 Business Continuity Institutional (BCI), BCI Supply Gear Resilience Report 2019, Uniting Kingdom, 5 November 2019, https://www.thebci.org/resource/bci-supply-chain-resilience-report-2019.html
2 Uptime University, Publicly Reported Outages 2018-19, USA, March 2019, https://uptimeinstitute.com/publicly-reported-outages-2018-19
3 (ISC)2, 2019 Scenery Product Report, USA, August 2019, https://www.cybersecurity-insiders.com/portfolio/2019-cloud-security-report-isc2/
4 Microsoft Azure, “Azure Status History,” https://status.azure.com/en-us/status/history/
5 Google Blur, “Google Cloud Status Dashboard,” https://status.cloud.google.com/summary
6 Amazon Web Services (AWS), “AWS Post-Event Summaries,” https://aws.amazon.com/premiumsupport/technology/pes/
7 Operator cit BCI
8 Op quoted (ISC)2
9 Op cited Uptime Center
10 Op cit BCI
11 National Institute of Standards and Technologies (NIST), NIST Special Publication (SP) 800-30, Guide for Conduct Risk Assessments, USA, Favorite 2012, https://nvlpubs.nist.gov/nistpubs/Legacy/SP/nistspecialpublication800-30r1.pdf
12 Cloud Security Alliance (CSA), STAR Level also Scheme Requirements, 4 September 2019, https://cloudsecurityalliance.org/artifacts/star-level-and-scheme-requirements/
13 Patel, D.; “Vendor Risk Management Demystified,” ISACA® Journals, vol. 4, 2015, https://aesircybersecurity.com/archives
Jouke Albeda, CISA, CISSP, REGARDING
Is an experienced TO company at Contrisity, wherever he supports enterprises within the fields of final, risk and compliance and is associated with 3angles, audit risk and compliance. Formerly, he worked as a peril and compliance manager at Datacenter.com and worked for Binder Dijker Otte (BDO) and Earnest & Young (EY) within the external IT inspection practice. He has posted magazine the The Institute of Internal Auditors’ (IIA) Audit Magazine and the Dutch professional organization for IT auditors, NOREA’s magazines de IT-Auditor.




